Civilization's maintenance backlog
A few dozen organization-shaped holes to be filled before powerful AI arrives
If you want to jump straight to our list of org-shaped holes, here it is. Otherwise… some context:
Atlas Computing has pivoted to forming new organizations to address critical gaps in AI deployment readiness and security infrastructure (or if you live in Berkeley, neglected catastrophic risks from AI).
In our previous post, we talked about how we updated our website to match this, and teased at sharing the list we’ve started. We’re excited to share our in-progress list.
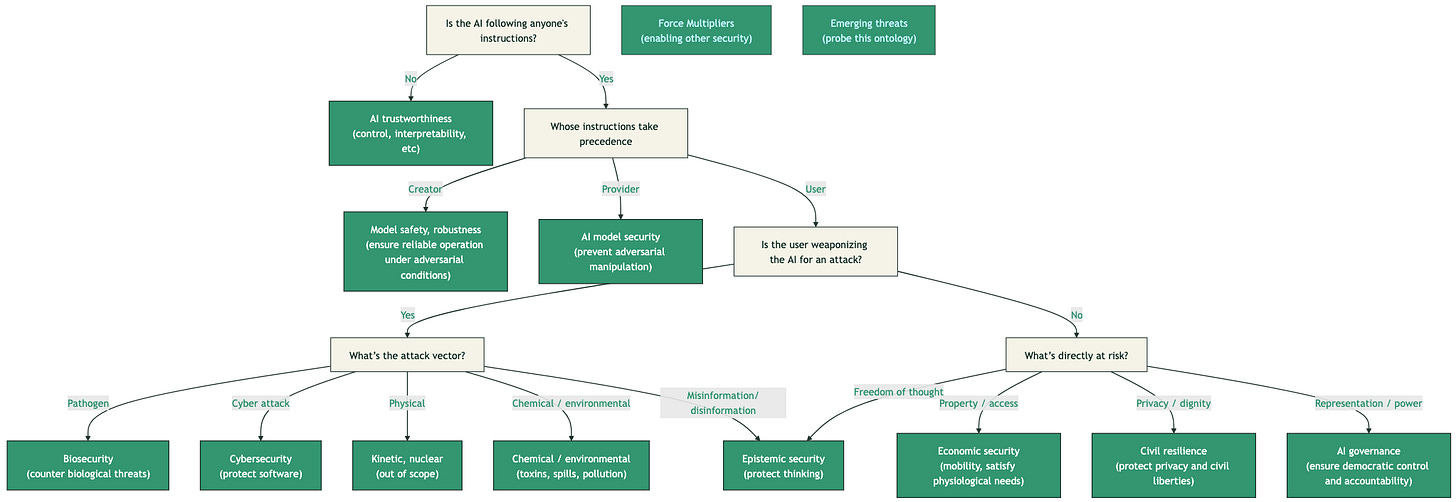
As a teaser, here’s the ontology we’re using for identifying categories of gaps:
This list of gaps is:
not comprehensive
We’d actually love to take suggestions of things we’re missing. If you have any ideas, please reach out to evan@atlascomputing.org, Or add a comment on this post or a comment on the sheet itself.
I did try to come up with some labels that feel mutually exclusive and completely exhaustive. I can’t guarantee I did a perfect job, but this seems like a relevant way of sorting possible orgs.
not very well-vetted
I think we got rid of all of the ideas that are clearly bad but some bad ones doubtlessly snuck through
not full of sexy startup ideas
These are not brilliant research directions or clever product insights. The expectations of these have you saying, huh, yes, full. And 20% you smacking your forehead wondering why no one’s built this yet.
not strictly nonprofits
As I’ve said before, we’re neither an incubator nor a fellowship program nor a think tank. We’ll try to get these orgs started (in a way that’s compliant with tax laws), but once someone can be the “go-to person” for that topic, we want to get out of the mix.
not a finished artifact
and it’s not trying to be. We could take forever just polishing this list and that would lead to nothing getting done. My favorite part of lists is crossing things off
just a to-do list of all of the orgs that we think someone should start, and we’ll do as many as we can as fast as we can.
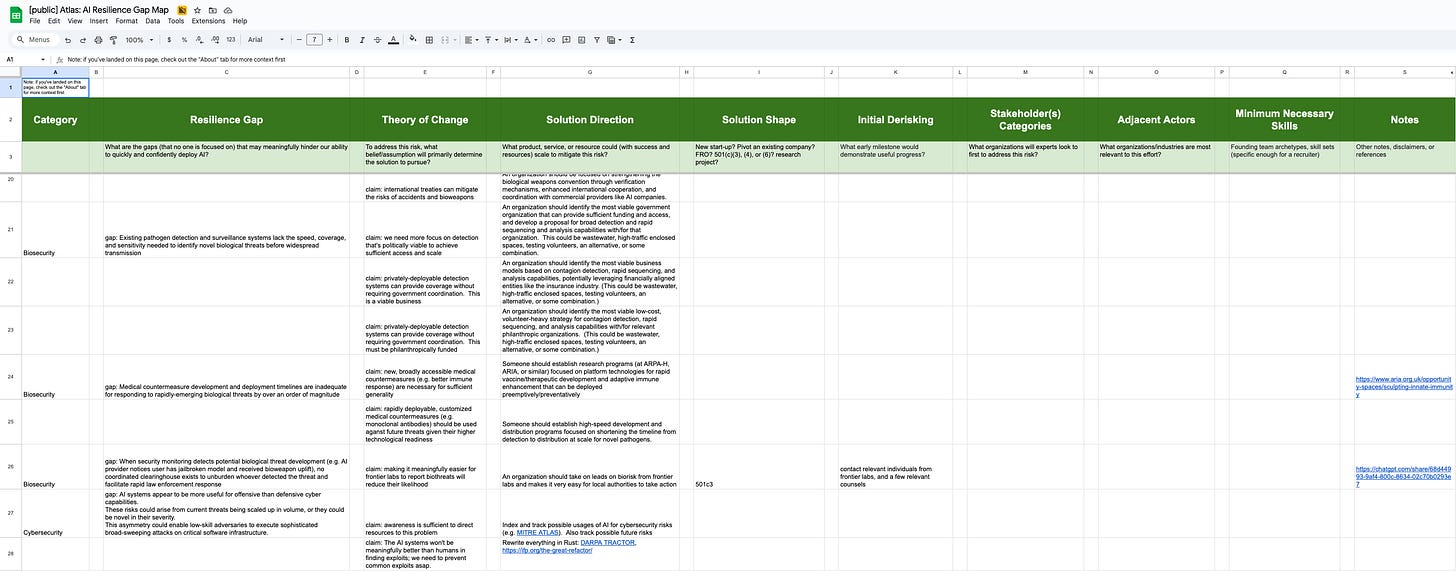
The plan is roughly to fill in the columns from left to right, and the columns are pretty specifically designed so that each column provides useful constraints to the next column to the right
linked at the bottom of the page
Most of these gaps don’t just create risks - they prevent confident, trustworthy adoption of what is already a very useful, transformational technology. When you can’t verify security properties, you slow down rollout. When you lack coordination infrastructure, you get duplicated effort. When you don’t have clear standards, it’s hard to blame people for repeated reinvention. We’re looking at reducing risks and increasing upsides.
the important part
However, the most important thing in this blog post by far is not the list. Rather, it’s the illustration of how to use the list. For one of these items, the biorisk clearinghouse (currently row 26), we’ve started an initial exploration of what it would look like to set up this organization.
Why this one? Because it’s concrete, clearly scoped, and has obvious stakeholders I could talk to immediately. Over the coming weeks, we’re interviewing relevant stakeholders to find out if this is really the problem, what hurdles make the problem challenging, and what skills are needed to jump those hurdles. After that, we’ll source someone with those skills and support them in starting the organization.
Maybe somewhere along the way we find this project isn’t necessary. I’d be delighted if someone beats us to it. But these things have gone unaddressed for long enough, I think it’s worth trying to do it ourselves.
Stay tuned to see our progress.
here’s the list
join this effort
Oh, and I’m trying to recruit a small team (2-10 others) to work with me on actually scoping out and starting these organizations. If you think that you (or someone you know) would be great at doing that, please reach out. We don’t have an official job description on the website, but the preview google doc is here. And if you can and want to join this cohort within your org, that’d be welcome too!